$2.18 Billion HSM Market Poised for Strong Growth by 2025: U.S., India, and Germany Drive Security Demand
The global HSM (Hardware Security Module) market is projected to grow from USD 1.71 billion in 2025 to USD 4.01 billion by 2033, at a CAGR of 11.23%.
- Last Updated:
HSM (Hardware Security Module) Market Q1 and Q2 2025 Forecast
The Hardware Security Module (HSM) market is projected to reach $2.18 billion in 2025, with a CAGR of 16.7% from 2025 to 2033. In Q1 2025, the market is estimated to generate approximately $544.6 million, fueled by increasing concerns over cybersecurity, data privacy, and compliance regulations. The U.S., India, and Germany are the leading markets for HSM, driven by the growing need to secure financial transactions, cryptographic data, and sensitive personal information. Cloud security, digital payment systems, and the adoption of blockchain technology are contributing to the demand for HSM solutions.
By Q2 2025, the market is projected to reach $552.9 million, as cloud-based security solutions become more widely adopted and the need for advanced encryption technologies grows. In India, the market is growing due to the increasing use of digital payments and e-commerce, while in Germany, strict data protection regulations are driving the adoption of HSM systems to ensure compliance with GDPR and other cybersecurity frameworks.
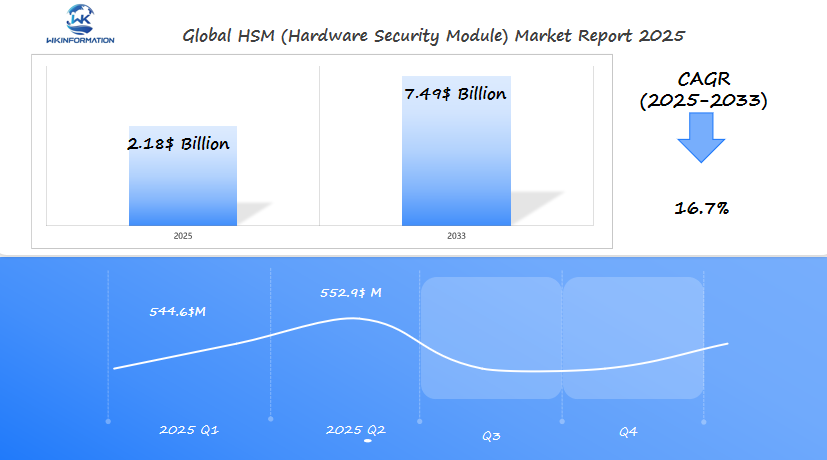
Key Takeaways
- HSM market growth is driven by U.S., India, and Germany’s focus on cybersecurity.
- Rising cyber threats and cloud adoption accelerate demand for HSM solutions.
- Regulatory compliance and data privacy laws boost HSM adoption in financial and governmental sectors.
- Cloud integration and payment security are key areas fueling this market expansion.
- HSMs remain vital for protecting sensitive information amid digital transformation.
Understanding the Upstream and Downstream Industry Chains for HSM (Hardware Security Module)
Hardware Security Modules (HSMs) rely on industry chains that connect raw materials to end-users. These industry chains begin with companies like Intel and ARM, who manufacture microchips for security purposes. Subsequently, logistics networks transport these components to manufacturers such as Thales and Utimaco, where the HSMs are assembled.
Upstream and Downstream Components
The upstream and downstream components of the HSM industry chain can be summarized as follows:
- Upstream: Chipmakers provide encryption processors; software developers create security algorithms.
- Downstream: Banks like JPMorgan and cloud platforms like AWS integrate HSMs for transaction protection.
The Role of Service Providers
Once the HSMs are deployed, service providers play a crucial role in maintaining their security by keeping them updated. This ongoing maintenance ensures that systems remain protected from potential threats.
The Strength of the Industry Chain
The network comprising suppliers, manufacturers, and end-users is robust. For example, Siemens utilizes HSMs in its industrial systems, thereby establishing a connection between the manufacturing and energy sectors.
The Importance of Understanding Industry Chains
Understanding these industry chains is beneficial for businesses as it enables them to:
- Address supply risks
- Identify new opportunities
From silicon production to server deployment, each component contributes to strengthening cybersecurity on a global scale.
Key Trends Driving the HSM Market: Rising Cybersecurity Threats and Cloud Integration
Hardware security modules (HSMs) are becoming more important as companies face more cybersecurity threats. They also need to grow their cloud operations. This shows the need for strong security tools to keep important data safe.
The Impact of Cybersecurity Threats
Cybersecurity threats are making companies rethink their security plans. Ransomware, phishing, and data leaks cost billions each year. HSMs help by keeping encryption keys safe and protecting sensitive data from unauthorized access.
Banks, for example, use HSMs to stop breaches and keep customer data safe.
The Role of Cloud Adoption
Cloud adoption is also a big factor. Companies are storing more data in remote servers. Laws like GDPR require encryption for this data.
- Real-time encryption keeps data safe during transfers between systems and the cloud.
The Significance of Cloud Integration
Cloud integration is a major reason for this demand. Over 70% of businesses now use hybrid cloud setups. HSMs are key for balancing growth and security. They help manage encryption keys centrally, reducing risks in networks.
Challenges in HSM Deployment: Compliance, Scalability, and Performance Issues
Setting up hardware security modules (HSMs) comes with its own set of problems. Compliance challenges are a big concern for companies. Rules like PCI DSS for payments or GDPR for data privacy are strict, making the process hard.
- Compliance: Meeting global standards without gaps
- Scalability: Adapting HSMs to growing data needs
- Performance: Balancing speed with security
| Sector | Key Standard | Example |
| Banking | PCI DSS | Payment processors must encrypt card data |
| Healthcare | HIPAA | Hospitals protect patient records |
| Government | FIPS 140-2 | Agencies secure classified systems |
Scalability tests often show how systems struggle under heavy loads. Slow performance can make transactions slow, losing customer trust. IBM and Thales provide solutions to meet changing compliance needs. Regular audits and flexible designs help manage these issues. Teams must focus on being adaptable while keeping security paramount.

Geopolitical Influence on the HSM Market
Geopolitics in security affects how countries choose to use hardware security modules (HSMs). Trade restrictions and sanctions limit access to key encryption tools. For example, U.S. export controls on crypto tech have blocked HSM sales in some areas, affecting global supply chains.
“Geopolitical tensions are now a core factor in enterprise security planning,” stated a 2023 Gartner report. “Companies must navigate regional policies to avoid disruptions.”
Nations like Germany and India are speeding up HSM adoption to fight off espionage threats. The EU’s Cybersecurity Act requires HSM use for data protection, boosting demand. At the same time, U.S. sanctions on Chinese tech firms have led to new HSM partnerships in Asia.
- Sanctions on Russian tech imports blocked access to Western HSM solutions.
- Trade agreements like the U.S.-Japan Digital Trade Agreement include clauses favoring secure hardware.
- Iran’s isolation has created niche markets for non-U.S. HSM providers.
As digital borders get stronger, businesses face a world divided by markets. Geopolitics in security now decides where HSM vendors grow, bringing both challenges and chances. The next decade will see security systems shaped by politics and technology alike
Types of HSM: General-Purpose, Payment, and Cloud-Based Security Modules
Choosing the right HSM types depends on specific security needs. Today, the market is dominated by three main categories:
- General-Purpose HSMs: These versatile modules protect data across industries. Banks, healthcare providers, and governments use them for encryption and key management. Brands like Thales Luna Network HSM and Utimaco’s Quantum Secure HSM offer broad flexibility.
- Payment HSMs: Designed for financial transactions, these meet PCI DSS compliance standards. Gemalto’s SafeNet and Yubico solutions secure payment gateways and card data, reducing fraud risks.
- Cloud-Based HSMs: Cloud providers like AWS CloudHSM and Microsoft Azure Key Vault HSM deliver scalable security for virtual environments. Ideal for SaaS platforms and hybrid IT setups, they integrate seamlessly with existing cloud infrastructure.
Businesses must align their choice with workflow demands. General-purpose HSMs handle diverse tasks, while payment-focused options prioritize transaction safety. Cloud-based solutions suit modern, distributed systems. Each type balances compliance, cost, and scalability—key factors in selecting the right tool for digital security challenges.
Applications of HSM in Banking, Cloud Security, and Enterprise Data Protection
Hardware security modules (HSMs) are changing how we protect important data. They play a key role in three main areas.
1. Banking
Banks use HSMs to keep transaction data safe and meet PCI-DSS standards. Companies like JPMorgan Chase and Visa use them to protect cardholder info. This helps lower fraud risks in online payments.
2. Cloud Security
Cloud providers like AWS and Microsoft Azure use HSMs to handle encryption keys. Services like AWS CloudHSM keep cloud data safe from unauthorized access.
3. Enterprise Data Protection
Companies use HSMs to protect their intellectual property. For example, IBM’s z16 mainframes have HSMs to encrypt sensitive files. This helps prevent data leaks in areas like healthcare and manufacturing.
HSMs are crucial in fighting cyber threats. A 2023 IBM study showed HSMs can reduce breach costs by 50% for users. HSMs are essential for protecting cloud data and financial transactions. As digital trust grows, these tools will become essential for businesses to stay safe and compliant.
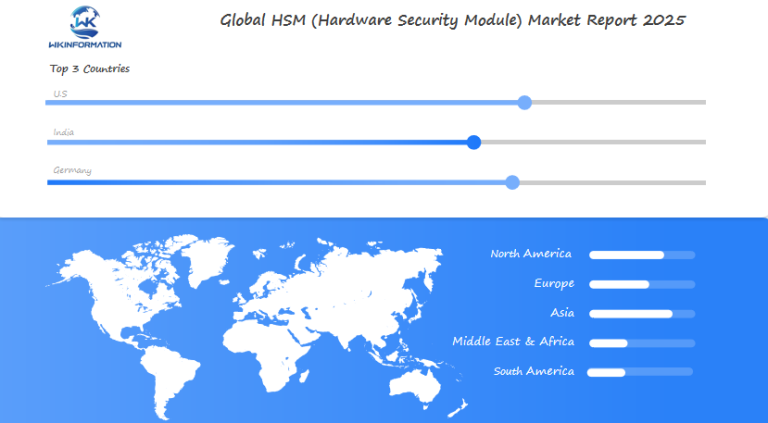
Global Insights into the HSM Market
The HSM market is changing fast, thanks to new tech and different needs around the world. In North America, the push for strong security in finance and healthcare is driving HSMs. In places like India and China, the growth of digital payments is pushing for cloud-based HSMs.
| Region | Key Drivers | Adoption Rate (2023) |
| North America | PCI DSS compliance | 78% |
| Europe | GDPR regulations | 65% |
| Asia-Pacific | E-commerce growth | 52% |
In Latin America and the Middle East, HSMs are being used to protect important projects. A Accenture study found that 60% of big companies are focusing on HSMs to fight ransomware.
- Cloud-first strategies are reshaping deployment models
- Post-quantum cryptography demands are rising in tech-savvy regions
- Regional partnerships drive localized HSM innovation
“The interplay between global market trends and localized compliance needs will define HSM’s trajectory,” says a Gartner analyst.
There’s a move towards using both on-premise and cloud HSMs. As cyber threats get more complex, companies are looking for flexible security solutions to keep up.
U.S. Market Demand for HSM in Financial Services and Government Sectors
The U.S. is leading the way in using hardware security modules (HSMs) to protect its financial security and government operations. Banks, payment processors, and federal agencies rely on HSMs to encrypt sensitive data, secure transactions, and comply with regulations such as PCI DSS and FedRAMP.
“HSMs are the backbone of digital trust in critical infrastructure,” states a 2023 report by the National Institute of Standards and Technology (NIST). Government agencies use HSMs to secure classified systems, while financial institutions deploy them to prevent fraud in real-time payments.
Key Use Cases for HSM in the U.S.
- Financial sector: Banks like JPMorgan Chase and Citigroup use HSMs to encrypt card data during transactions.
- Government: The Department of Defense and IRS rely on HSMs to protect classified networks and tax records.
- Compliance: Over 70% of U.S. financial firms now integrate HSMs to meet federal cybersecurity mandates.
Recent attacks, such as the 2021 Colonial Pipeline ransomware incident, highlight the urgency of this need. HSMs provide tamper-resistant hardware to safeguard cryptographic keys, reducing the risk of breaches. Federal grants and partnerships are currently funding upgrades to HSM systems in critical sectors.
Shifting Focus Towards Cloud-Compatible HSM Solutions
As cyber threats continue to grow, the U.S. market is placing a greater emphasis on HSM solutions that are compatible with cloud platforms like AWS and Azure. Leading companies such as Thales and Utimaco are at the forefront of this shift, offering tailored solutions for federal and financial requirements.
With over $450 million allocated for federal cybersecurity initiatives in 2024, there is an expected increase in demand for HSM-based systems that ensure the security of U.S. financial operations.
India’s Expansion in HSM Adoption for Secure Digital Transactions
India is making significant progress in digital security. With over 800 million internet users, it’s crucial to protect financial data. Initiatives like Digital India and the Unified Payments Interface (UPI) are at the forefront of this effort.
Banks and fintech companies are turning to hardware security modules (HSMs) to combat cyber threats. This strategy is essential for ensuring secure digital transactions.
Key drivers:
- Rapid growth of digital payments (UPI processes 2.5 billion transactions daily).
- Regulatory requirements for a secure banking infrastructure.
- Increasing adoption of HSMs by rising fintech startups such as Paytm and PhonePe.
India’s digital security journey is both exciting and challenging. Small businesses and rural areas are embracing HSMs for e-commerce and mobile banking. Companies like Gemalto and Thales are experiencing a surge in demand from Indian banks.
Experts believe this trend will increase India’s role in the global HSM market. It will also lead to new partnerships between local and international tech firms.
The RBI’s cybersecurity guidelines are making HSMs a necessity for online transactions. As India expands its digital payments, it sets a powerful example of how emerging economies can balance growth with safety.
Germany’s Leadership in HSM Innovation for Enterprise Cybersecurity
Germany is known for its precision engineering, which drives its German innovation in cybersecurity. Companies like Thales and Utimaco are at the forefront. They create hardware security modules (HSMs) that safeguard financial transactions and government data.
Their solutions are at the cutting edge of technology and meet strict compliance standards. This makes them leaders worldwide.
Some key advancements include:
- Quantum-resistant encryption to counter future cyber threats
- Hybrid HSM systems blending on-premise and cloud security
- Automated compliance tools for real-time regulatory checks
German companies work with the Bundesamt für Sicherheit in der Informationstechnik (BSI) to set global standards. Their focus on interoperability ensures HSMs work well across different industries. For U.S. businesses, using these solutions means getting access to proven technology with decades of research and development.
German innovation is crucial in protecting payment systems and government networks. This focus on reliability makes Germany a leader in the global HSM race.
The Future of HSM: AI-Powered Security and Post-Quantum Cryptography
Future technologies in HSM are changing cybersecurity. AI and post-quantum cryptography are making data protection better. They aim to beat even the toughest cyber threats.
How AI is Transforming Cybersecurity
AI is playing a crucial role in enhancing cybersecurity measures. Here are some ways in which AI is transforming the field:
- Automated threat detection in real time.
- Learning patterns to predict and block attacks.
- Reducing human oversight needs for security tasks.
The Significance of Post-Quantum Cryptography
Post-quantum cryptography is also important. It helps HSMs deal with quantum computers. Traditional encryption might not work against them. But, new algorithms from NIST keep data safe.
Companies like IBM and Microsoft are testing these new methods. They want to protect important data.
Experts think these technologies will be key by 2030. AI and quantum-resistant encryption together offer strong protection. This is great for banking and healthcare, making them safer.
HSMs need to change to keep up with digital threats. AI and post-quantum tech are crucial. Companies that invest now will lead in digital security.
Competitive Landscape in the HSM Market
- Thales Group
- Utimaco GmbH
- IBM Corporation
- Futurex
- Atos SE
- Infineon Technologies AG
- STMicroelectronics
- Microchip Technology Inc.
- Entrust Corporation
- Yubico
Overall
| Report Metric | Details |
|---|---|
| Report Name | Global HSM (Hardware Security Module) Market Report |
| Base Year | 2024 |
| Segment by Type |
· General Purpose HSMs · Payment HSMs · HSMaaS |
| Segment by Application |
· Financial Services · Healthcare · Government and Defense · Cloud Service Providers |
| Geographies Covered |
· North America (United States, Canada) · Europe (Germany, France, UK, Italy, Russia) · Asia-Pacific (China, Japan, South Korea, Taiwan) · Southeast Asia (India) · Latin America (Mexico, Brazil) |
| Forecast units | USD million in value |
| Report coverage | Revenue and volume forecast, company share, competitive landscape, growth factors and trends |
The HSM market is growing fast as more industries focus on keeping data safe. Cyber threats and the move to cloud services are big reasons for this growth. The U.S., India, and Germany are leading the way in using HSMs in banking and government.
Even with challenges like rules and growing needs, new tech like AI and quantum cryptography are changing HSMs. Choosing the right HSM for your business means knowing about new risks. Working together, tech companies and users can meet today’s needs and prepare for the future.
With more online deals happening, companies need to keep their HSM plans up to date. HSMs are key for keeping financial and government data safe. Keeping up with new tech helps businesses protect their assets while still growing.
Global HSM (Hardware Security Module) Market Report (Can Read by Free sample) – Table of Contents
Chapter 1: HSM (Hardware Security Module) Market Analysis Overview
- Competitive Forces Analysis (Porter’s Five Forces)
- Strategic Growth Assessment (Ansoff Matrix)
- Industry Value Chain Insights
- Regional Trends and Key Market Drivers
- HSM (Hardware Security Module)Market Segmentation Overview
Chapter 2: Competitive Landscape
- Global HSM (Hardware Security Module)players and Regional Insights
- Key Players and Market Share Analysis
- Sales Trends of Leading Companies
- Year-on-Year Performance Insights
- Competitive Strategies and Market Positioning
- Key Differentiators and Strategic Moves
Chapter 3: HSM (Hardware Security Module) Market Segmentation Analysis
- Key Data and Visual Insights
- Trends, Growth Rates, and Drivers
- Segment Dynamics and Insights
- Detailed Market Analysis by Segment
Chapter 4: Regional Market Performance
- Consumer Trends by Region
- Historical Data and Growth Forecasts
- Regional Growth Factors
- Economic, Demographic, and Technological Impacts
- Challenges and Opportunities in Key Regions
- Regional Trends and Market Shifts
- Key Cities and High-Demand Areas
Chapter 5: HSM (Hardware Security Module) Emerging and Untapped Markets
- Growth Potential in Secondary Regions
- Trends, Challenges, and Opportunities
Chapter 6: Product and Application Segmentation
- Product Types and Innovation Trends
- Application-Based Market Insights
Chapter 7: HSM (Hardware Security Module) Consumer Insights
- Demographics and Buying Behaviors
- Target Audience Profiles
Chapter 8: Key Findings and Recommendations
- Summary ofHSM (Hardware Security Module)Market Insights
- Actionable Recommendations for Stakeholders
Access the study in MULTIPLEFORMATS
Didn’t find what you’re looking for?
TALK TO OUR ANALYST TEAM
Need something within your budget?
NO WORRIES! WE GOT YOU COVERED!
Call us on: +1-866-739-3133
Email: infor@wkinformation.com
What is a Hardware Security Module (HSM)?
A Hardware Security Module (HSM) is a physical device that manages digital keys for strong authentication and provides cryptographic processing. HSMs protect sensitive data and ensure secure transactions across various industries.
Why is the HSM market expected to grow significantly by 2025?
The HSM market is expected to grow to $2.18 billion by 2025. This growth is due to rising cybersecurity threats and the need for secure transactions. Cloud services in businesses also play a role. Key players from the U.S., India, and Germany are driving this demand.
How do geopolitical factors influence the HSM market?
Geopolitical factors such as international relations and economic sanctions have an impact on the HSM market. They can affect market access and influence technology adoption, which in turn shapes the global demand for secure hardware solutions.
What types of HSMs are available in the market?
There are different types of HSMs, including general-purpose modules and payment-specific modules. Cloud-based security modules are also available. Each type has unique features and benefits for different applications. It’s important to choose one that meets your specific security needs.
How are HSMs applied in different sectors?
HSMs are used in various sectors:
- In banking, they ensure secure transactions.
- In cloud security, they protect data.
- In enterprise data protection, they enhance overall cybersecurity.
Each sector uses HSM technology to strengthen security and protect sensitive information.
What challenges do organizations face when deploying HSM solutions?
Organizations face challenges like compliance with regulations and scalability of solutions. Performance issues can also arise. Successfully addressing these challenges is key to maintaining high security standards while integrating HSMs into existing systems.
Key Trends Shaping the HSM Market
The HSM market is being shaped by several key trends:
- Escalating cybersecurity threats: As cyberattacks become more sophisticated and frequent, organizations are increasingly investing in robust security measures to protect their sensitive data.
- Integration of cloud services: With the widespread adoption of cloud computing, businesses are looking for secure ways to manage their cryptographic keys and protect data stored in the cloud. HSM solutions offer a reliable way to achieve this.
These trends are driving organizations to embrace HSM technologies as an essential component of their security strategies.
What does post-quantum cryptography mean for HSM technology?
Post-quantum cryptography refers to systems designed to be secure against quantum computers. This technology is being integrated into HSMs. It enhances data protection and ensures long-term security solutions against evolving digital threats.
How do different countries contribute to HSM innovation?
Countries like Germany are leading in HSM innovation, developing advanced technology solutions. Nations like India are rapidly adopting HSMs to support their fintech sectors. This contributes to the global advancement of hardware security solutions.
What factors should businesses consider when choosing an HSM?
Businesses should consider security requirements, scalability, and compliance with industry standards. The type of integration needed with existing systems is also important. It’s essential to align the HSM choice with the organization’s overall cybersecurity strategy.


